Figure 2.2: Enabling an option
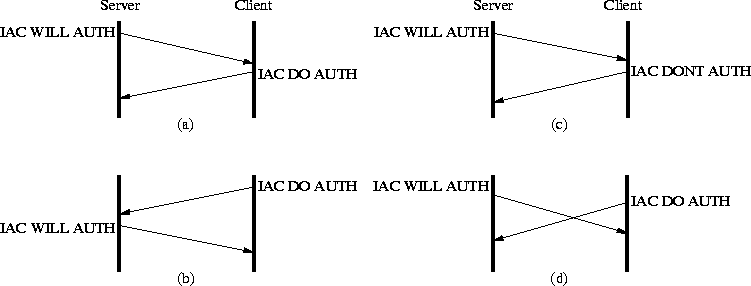
The time sequences in figure 2.2 illustrates some possible option code exchanges when one or both of the parties want to enable an option.
In cases (a) and (b), both parties want the server to enable the AUTH option. In (a) the server request this, while the client request it in (b). The server want to enable AUTH in (c), but the client does not support it, and responds with a negative acknowledge. (d) shows the case when both parties, simultaneously, want the server to enable the option. They will both see the received request as an acknowledge of their own request.

Figure 2.2: Enabling an option
Figure 2.3 shows the use of sub-negotiation for the ABC option. This option requires one argument before it can take effect. In (a), the server want the client to enable the option. In (b), the client want to enable the option. If any of these initial negotiations had not been successful, no sub-negotiation would take place. (c) shows the server sending the required argument to the client. The client will now ``do'' ABC arg.
The description of the AUTHENTICATION option in section 2.10 will give more examples of how sub-negotiation is used.