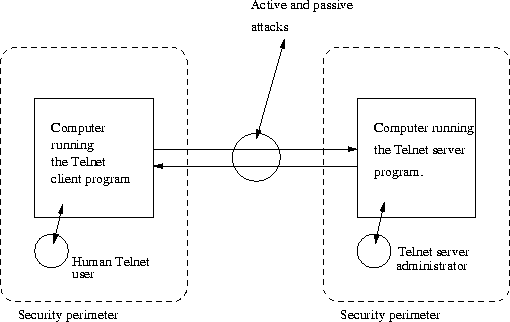
Figure 3.1: Secure Telnet Environment

Figure 3.1: Secure Telnet Environment
Figure 3.1 illustrates the assumed environment where Secure Telnet will be used. It is important to note that the client user and server administrator are located inside the security perimeter. These persons can violate the security of the system by giving away key material to an adversary. They must therefore have a security clearance before they are granted access to use Secure Telnet. All attacks are assumed to be on the communication link, but the attacker may know everything about the protocol specification and for instance, the random number sources used.