Next: Format of the ``challenge''
Up: PGP authentication scheme
Previous: PGP authentication scheme
The authentication information is the data block which is sent by the party
which want to be authenticated.
This data block must have the
following properties.
- Make it possible for the receiver to verify that the origin of the
data really is the claimed originator.
- Impossible for an adversary to interpret (contains secret session keys).
- Not be valid if an active intruder replays a previously recorded
data block.
The PGP program package offers functions which help accomplish these
properties. The properties, except number 3 (replay attacks), can
easily be accomplished by
using digital signatures and public key encryption.
The replay attack is generally the most difficult attack to handle in
authentication
systems. It could be solved by adding a time stamp to the data which are
signed. SPX authentication will probably use this solution [4].
The server (or client) can then reject authentication information
with an old time stamp .
This method requires the client and server system clocks to be synchronized.
This can not be guaranteed, as network time protocols in use today are not
secure. An resourceful attacker can easily manipulate the system clock in a
server, and then replay old authentication information.
.
This method requires the client and server system clocks to be synchronized.
This can not be guaranteed, as network time protocols in use today are not
secure. An resourceful attacker can easily manipulate the system clock in a
server, and then replay old authentication information.
Another method which solves the authentication problem is to include a
sequence number or a random number in the signed data block. The server
would then have to remember which number is the next in sequence for all
clients. If a
random number is used, the server would have to remember all previously
used numbers. This increases system complexity.
Because of the deficiencies of these solutions, another solution was
chosen, the challenge-response authentication scheme. This scheme
works as follows.
Suppose Alice is to be authenticated by Bob. Bob will send an
challenge to Alice. The challenge may be a random number. Alice will
then perform some secret operation on this number or digitally sign the
number. The result of this operation is the response. She then sends
the response to Bob, who will verify the performed operation or digital
signature. If the verification was successful Bob knows that he is talking
to Alice. Alice is the only one who can produce this response.
This method
implies one more Telnet sub-option transmission, but this can be justified
since:
- Client and server system clocks need not be synchronized.
- The server does not need to have a database with previously used
sequence numbers.
- Transmission speed is usually not a problem in networks where Telnet
is used.
The following data structure definition shows the format of the
authentication information before any processing by PGP. This data
structure meets the authentication design goals. The MPI
type is described in section 2.8.3.
BEGIN
MPI challenge
MPI my_encryption_key
MPI your_encryption_key
END
- challenge
- is the the random number received from the party we want
to be authenticated by.
- my_encryption_key
- is the random session key the sender of this
authentication information want to use for bulk data encryption.
- your_encryption_key
- is the random session key the sender of this
authentication information want to use for bulk data decryption.
This data structure is denoted by M. Then the steps of signing and
encrypting this message can be written:

Where 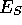 is encryption with the private key of the sender, and
is encryption with the private key of the sender, and 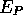 is
encryption with the public key of the receiver.
is
encryption with the public key of the receiver.
However, this method is not used in PGP as it will be very slow if the
length of the message M is
large. PGP uses instead IDEA for encryption and signing the MD5 message
digest, see chapter 2.7. By using PGP for the encryption and signing, we
will get a well defined, processor independent, message format.
The authentication-information format is defined to be equal to what
PGP produces when it is invoked to sign and encrypt a message. If the data
structure, M, resides in a file called ``authstruct'', the following command
invokes PGP to create authentication-information.
pgp -se authstruct Receiver_Name
The authentication-information will then be stored in a file called
``authstruct.pgp''. This file can only be decrypted by ``Receiver_Name''.
After decryption, the receiver can check the signature to verify the
authenticity of the data.
An
attacker will not be able to see who is sending the authentication-information,
as only ``Receiver_Name'' will be able to see who has signed the message.



Next: Format of the ``challenge''
Up: PGP authentication scheme
Previous: PGP authentication scheme
Asgaut Eng
Wed Apr 10 14:07:30 MET DST 1996
 .
This method requires the client and server system clocks to be synchronized.
This can not be guaranteed, as network time protocols in use today are not
secure. An resourceful attacker can easily manipulate the system clock in a
server, and then replay old authentication information.
.
This method requires the client and server system clocks to be synchronized.
This can not be guaranteed, as network time protocols in use today are not
secure. An resourceful attacker can easily manipulate the system clock in a
server, and then replay old authentication information.