Next: Encryption option
Up: Authentication option
Previous: Sub-option command meanings
This section describes the negotiation and sub-negotiation of an
authentication procedure. Please refer to figure 3.2
while reading this.
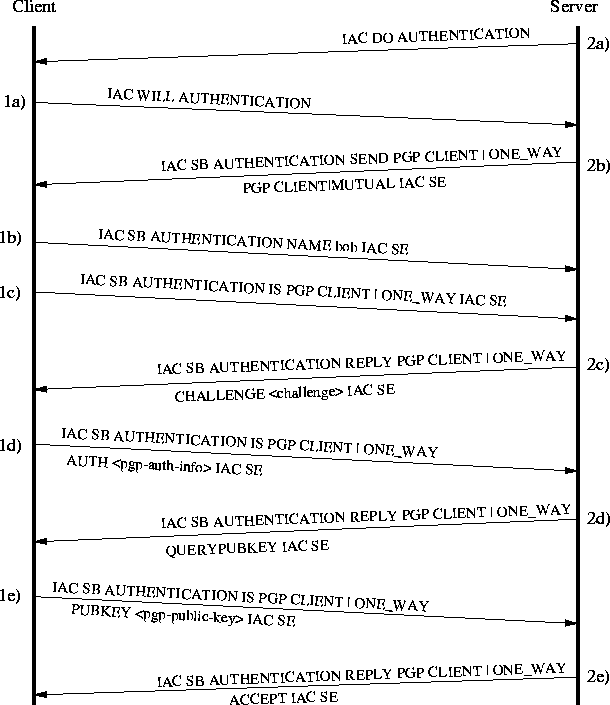
Figure 3.2: Typical PGP authentication procedure
- 1a),2a)
- Initial negotiation to use the AUTHENTICATION option.
- 2b)
- The sub-negotiation then begin as the server sends the list of
supported authentication types. This server prefers one-way client to
server authentication, but is also willing to do mutual authentication
where the client sends its authentication information first.
- 1b,1c)
- The client picks an authentication type and sends the name of the
user it wants to log in as and the selected authentication type. These two
messages may be sent in any order.
- 2c)
- The server then sends the challenge, which the client must
include in the authentication information.
- 1d)
- Now the client builds the PGP authentication information and
sends it.
- 2d)
- For this particular client the server did not have the public
key, so it asks for it by sending a QUERYPUBKEY.
- 1e)
- The client responds by sending its public key.
- 2e)
- The server verifies the signature in the
authentication information message and any signatures on the public key. As
these tests are OK and the owner of the key is granted access it responds
with an ACCEPT message.
Asgaut Eng
Wed Apr 10 14:07:30 MET DST 1996

