 .
.
The encryption/decryption of the Telnet session must be a service provided by the Telnet client and server applications. This is stated in the encryption design goals.
The Network Virtual Terminal concept used in Telnet gives two possible places to insert an encryption/decryption module. Figure 3.3 a) shows the placement proposed by Borman's draft. This placement will only encrypt the user data. An attacker can in many cases learn much about what is communicated by just reading the unencrypted option sequences. Some option codes also transfer information which should be kept secret, e.g. the ENVIRON [18] option which transfers user environment variables.
Figure 3.3 b) shows a better placement of the
encryption/decryption module. In this case all information exchanged
between the Telnet applications are encrypted .
.
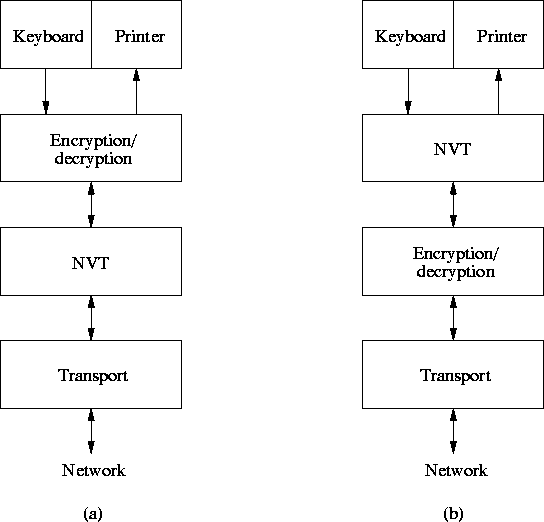
Figure 3.3: Possible placements of the encryption/decryption module