Next: Integrity option
Up: Encryption option
Previous: Command meanings and usage
Figure 3.5 shows a typical Telnet session involving data
encryption in one direction.
- 1a),2a)
- Initial negotiation to use the ENCRYPT option. (Host 2
wants Host 1 to send encrypted data).
- 2b)
- Host 2 sends the list of supported encryption types.
- 2c)
- Host 2 requests Host 1 to begin encrypting its data stream with
encryption type 1.
- 1b)
- Host 1 selects encryption type 2 as it did not support the
requested type. All data following the IAC SE sequence in this command are
now encrypted.
- 2d)
- Host 2 has received all the information which needed to be
encrypted, and requests Host 1 to stop encrypting.
- 1c)
- Host 1 informs Host 2 that the encryption is being turned off
after the IAC SE sequence in this message.
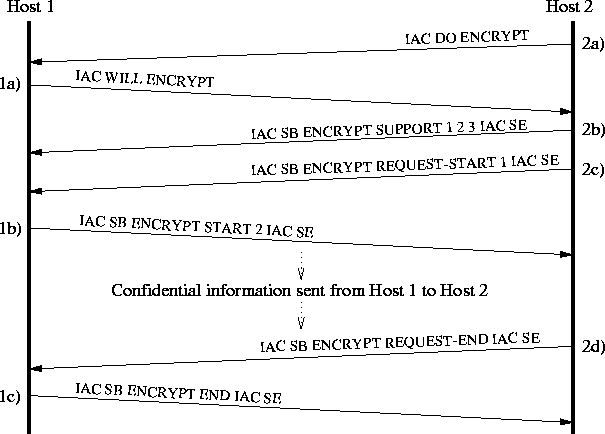
Figure 3.5: Example of a session with encryption
Asgaut Eng
Wed Apr 10 14:07:30 MET DST 1996

